One of the technologies key to the ongoing evolution of the Internet that we pay close attention to here at Pulse is secure Internet routing with RPKI. Like all fundamental Internet technology, initial deployments of Internet routing protocols were completely insecure. Over time, as more valuable transactions have occurred over the Internet, pressure has grown to make the underlying infrastructure more dependable. Security has a vital role to play in this.
Internet routing protocols determine how messages from one Internet host (computer) reach the correct destination. These protocols allow the thousands of networks that compose the global Internet to interconnect and route traffic to and from each other without needing pre-arranged agreements (beyond supporting the same routing protocol).
Internet traffic can be accidentally or deliberately re-routed without additional security measures, creating surveillance and denial-of-service risks.
What Is RPKI?
There are two main elements to enhancing Internet routing security with RPKI. The first is for network operators to publish Route Origin Authorizations (ROAs). ROAs are cryptographically signed objects that state which Autonomous System (AS/network) is authorized to originate a particular IP address prefix or set of prefixes. This is where the PKI (Public Key Infrastructure) part of RPKI comes in, as these ROAs are certified in a chain of trust up to a Trust Anchor.
The second element in the RPKI framework is for network operators to import Trust Anchors and use them to verify ROAs published by other networks. The verified list of prefixes, maximum lengths, and origin AS numbers provide a set of Validated ROA Payloads (VRPs) for routing decisions.
Measuring Adoption
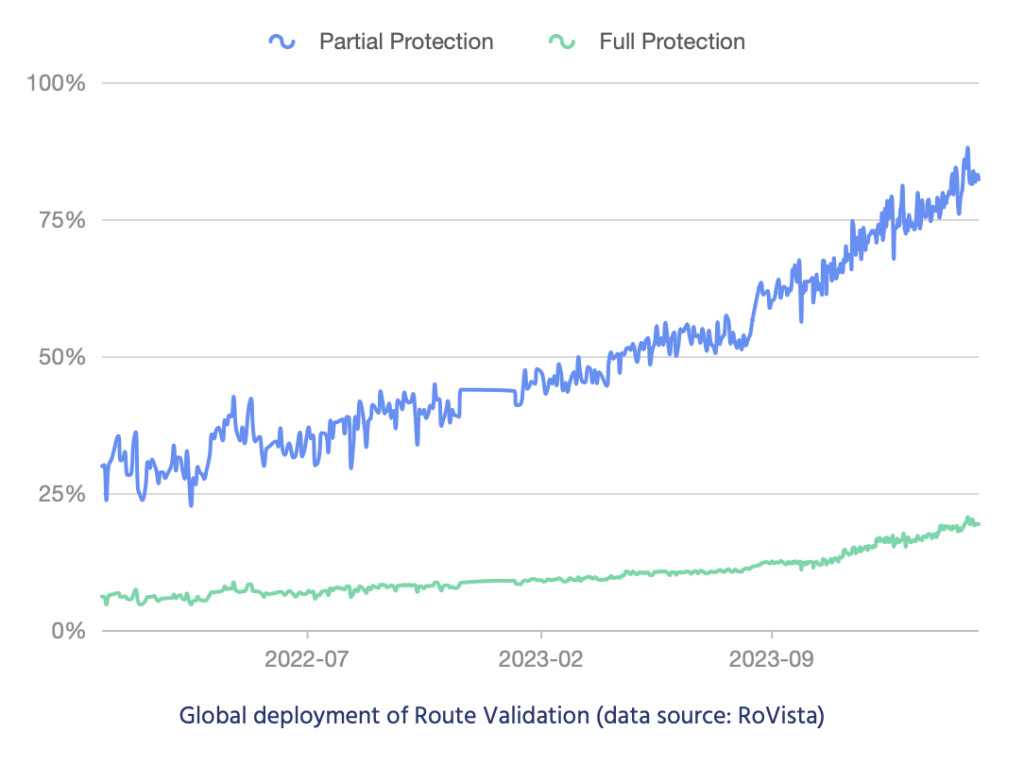
On Pulse, we monitor network operators’ route validation adoption using RoVista data. Their measurement technique provides us with two insights: the percentage of networks that benefit from complete protection of their routes and the percentage of networks that benefit from partial protection. This latter category may be network operators that, while they do not perform route validation themselves, get connectivity from networks that do and thereby gain some security benefit from that validation.
According to RoVista’s metric, in 2023, partially protected networks nearly doubled from 44% to 81%, while fully protected networks saw a similar level of growth, going from 9% to 18%. This remarkable growth shows that the deployment of RPKI verification by larger transit networks is disproportionately impacting protection for their downstream customers. It would be nice if every network operator validated routes using RPKI. Still, we don’t need that to be the case for widespread benefits to accrue from RPKI adoption by major transit network operators.
Today, more than half the networks in the global Internet routing system are listed as Origin AS in at least one ROA. ROAs cover the majority of unique IPv6 prefix-origin pairs in the default-free zone, and the IPv4 routing table is likely to reach the same milestone in the coming weeks. Similarly, most advertised IPv6 address space is covered by a valid ROA.
Learn More and Take Action
These metrics indicate a very healthy adoption of RPKI amongst some of the global key network operators. If you’d like to learn more about the importance of routing security for the future of the Internet and what network operators worldwide are doing to collaborate on improving the communications infrastructure so many of us have come to depend on, check out MANRS.
Photo by Brett Jordan on Unsplash


